Enhancing Oil and Gas Security: The Role of Surveillance Systems in Protecting Critical Infrastructure
The oil and gas industry is one of the most crucial sectors for global economic stability, but it's also one of the most vulnerable to security...
8 min read
Turn-key Technologies Staff : April 12, 2024
Did you know that cybercrime is projected to cost the world $10.5 trillion annually by 2025, according to Cybersecurity Ventures? This figure highlights an urgent need for better online security measures. Among the tools at the disposal of technology leaders, proxy servers stand out as a critical component in safeguarding online activities and enhancing data privacy, especially in sectors where sensitive transactions and data exchanges occur frequently.
Proxy servers, acting as intermediaries between user devices and the internet, offer a layer of anonymity and security by masking users' real IP addresses. This mechanism is crucial for businesses aiming to protect their digital assets and maintain confidentiality in their operations. In contrast to VPNs, which encrypt all internet traffic, proxies provide a targeted solution for specific internet activities, making them a versatile tool for different scenarios, such as web scraping, SEO monitoring, accessing geo-restricted content, and enhancing privacy.
However, the decision to use a proxy server over a VPN or other security measures should be informed by the specific needs and online behavior of the business. While proxy servers excel in hiding IP addresses and bypassing geo-restrictions with minimal impact on internet speed, they do not offer the same level of data encryption as VPNs. Therefore, technology leaders must weigh the benefits of using proxy servers, such as improved network performance and targeted anonymity, against their limitations, including the lack of encryption for all types of internet traffic and potential vulnerabilities to data interception.
TL;DR Summary: This blog post discusses the critical role of proxy servers in enhancing online security and privacy, especially in the face of escalating cyber threats. It highlights the importance of these tools in protecting digital assets, maintaining confidentiality, and enabling efficient online operations. By comparing the functionalities of proxy servers with those of VPNs, it provides technology leaders with insights into when and why to choose proxies for their specific online security needs. The post emphasizes the strategic decision-making process involved in selecting the right online security measures, emphasizing the need for a balanced approach to safeguarding sensitive information and ensuring strong data protection in the digital age.
A proxy server operates as a distinct unit, equipped with its own IP address that's linked to a specific geographical location. Utilizing a proxy creates a protective layer between your device and the immensity of the internet. Essentially, it ensures that your real IP address, geographical location, and any other sensitive details remain undisclosed. It's like borrowing another's device or IP address for web access or online activities. This mechanism enables anonymous web surfing, beneficial to a broad spectrum of users. Whether for personal use or corporate applications, proxies enhance online operations by enhancing efficiency and security, especially when sourced from dependable suppliers specializing in private or dedicated proxies.
Proxies are invaluable for those prioritizing online anonymity, safety, and unrestricted web access. While there's a common tendency to mix up proxy servers with VPNs due to their shared goal of protecting online identities, the two operate distinctly.
Understanding the nuances of proxy servers is important for enhancing network functionality and security. Proxy servers act as intermediaries between end users and the websites or services they wish to access, providing a necessary layer of privacy and control. Among the many types of proxy servers, each offers unique features for specific needs and use cases.
First up, the Forward Proxy stands as the most common type, primarily used in corporate networks. It acts on behalf of users, sending requests to the internet. This type of proxy is instrumental in content filtering, monitoring employee internet usage, and providing shared network connections. Forward proxies serve a crucial function by circumventing geo-restrictions, granting users the ability to reach content that may be otherwise inaccessible in their specific location.
Conversely, Reverse Proxies function as intermediaries for web servers, efficiently routing client requests to the designated server. In contrast to forward proxies that handle outbound requests, reverse proxies excel in managing inbound requests, offering advantages such as load balancing, ensuring anonymity for backend servers, and boosting security and speed with SSL encryption and content caching, respectively.
Transparent proxies seamlessly direct requests without modifying them or requiring any configuration on the user's part, making them invisible to the end-user. They are often used by organizations and ISPs for content filtering and data caching but offer no anonymity since the original IP address remains visible.
Anonymous proxies prioritize privacy, hiding the user's IP address to ensure anonymity online. These proxies are favored by individuals looking to shield their browsing habits from the eyes of ISPs and websites, although they can sometimes be slower due to the additional privacy measures.
Distorting proxies are similar to anonymous proxies but take anonymity a step further by presenting a false IP address to websites, making it even more difficult to trace the user's location and identity.
And last but not least, High Anonymity proxies, or Elite proxies, offer the highest level of privacy and security. They conceal both the user's IP address and the fact that a proxy is being used, making it almost impossible for websites to detect the presence of a proxy. These are particularly favored for sensitive tasks that require a high degree of anonymity.
Each type of proxy server offers distinct advantages and limitations, catering to various needs within the IT landscape. By having a good understand of the various types of proxy servers, IT professionals can more effectively customize their network infrastructure to enhance security, uphold privacy, and optimize network performance.
While both proxy servers and VPNs can provide anonymity and privacy, there are some key differences between them. A proxy server only handles web traffic and specific applications, while a VPN encrypts all internet traffic from the user's device. Proxy servers and VPNs serve the purpose of improving online privacy and accessing restricted content, but they do so in different ways and with varying degrees of effectiveness.
Proxies act as gateways, offering a basic level of anonymity by hiding your IP address without encrypting your data, making them suitable for bypassing geo-restrictions on websites.
VPNs, on the other hand, not only hide your IP address but also encrypt your entire internet connection, providing a much higher level of security and privacy. This encryption is particularly important in protecting sensitive information from hackers, especially when using public Wi-Fi networks. While proxies can be faster due to the lack of encryption, VPNs offer comprehensive protection, making them a better choice for those who prioritize security over speed.
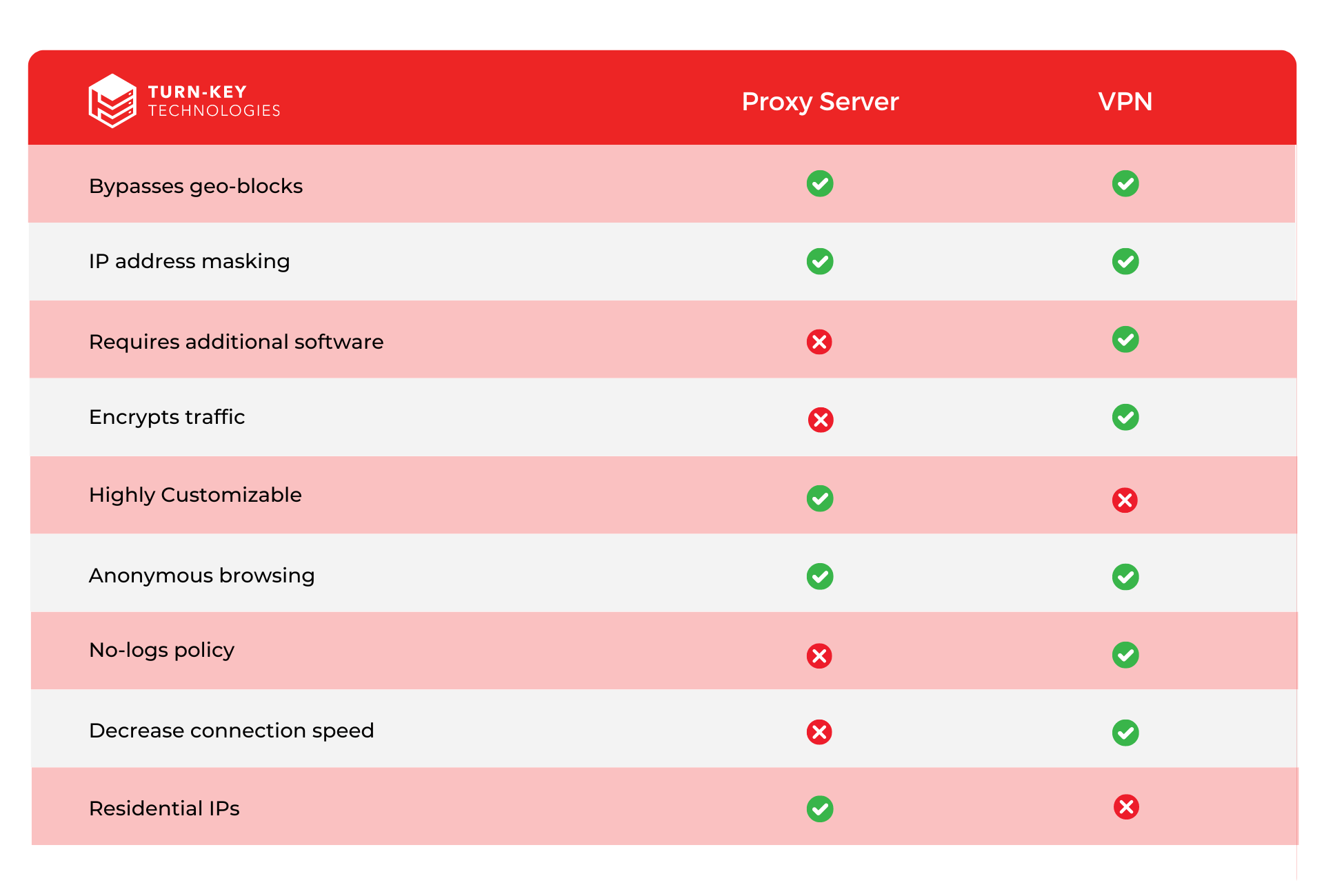
Another difference is that proxy servers can be configured on a per-application basis, allowing users to choose which applications route their traffic through the proxy. On the other hand, VPNs encrypt all traffic by default, regardless of the application.
Additionally, VPNs provide a higher level of security as they create a secure and encrypted connection between the user's device and the VPN server. This ensures that all data transmitted between the two endpoints is protected from eavesdropping or interception.
A proxy serves as a middleman between your device and the vast expanse of the internet, effectively substituting your IP address with its own to manage your online interactions. Opting for a proxy to employ an IP address that isn't your own offers numerous benefits, primarily granting you greater command over your digital footprint. This control allows you to dictate the extent of personal information that websites and online services can accumulate about you.
This brings us to the question: What makes the use of proxies advantageous, and who stands to benefit from their use? This discussion dives into the four predominant scenarios where proxies find their utility.
Web scraping refers to the automated process of extracting data from the web. This technique is utilized by both companies and individuals for a variety of reasons, such as market research, generating leads, collating price information, and beyond. Given that many online platforms restrict the volume of requests from a single IP address, proxies emerge as a crucial tool for circumventing such limitations. By assuming different IPs in varied locales, proxy servers enable scrapers to mimic the activity of legitimate site visitors, thereby eluding detection and blocks on scraping activities.
For the majority of businesses today, search engine optimization (SEO) is non-negotiable. Considering that a mere 0.63% of users venture beyond the first page of Google's search results, it's clear why SEO tracking has become essential. Achieving and maintaining a high search engine ranking not only boosts organic traffic and client acquisition but also fosters brand recognition and revenue growth over time. Regularly monitoring search engine results pages (SERPs) and competitor websites is vital. Through the use of proxy servers, businesses can perform searches from various IPs and locations, yielding invaluable insights for refining SEO strategies to better meet their target audience.
Geo-restrictions are a common barrier that restricts access to certain websites and online services based on the user's geographic location. While these restrictions can sometimes be justified by legitimate copyright and licensing concerns, they can also be applied unfairly. This is where proxy servers come into play, offering a simple yet effective solution to bypass these limitations. By utilizing a proxy server located in a region where the desired content is accessible, users can effortlessly navigate around these restrictions in a secure and private manner. Proxies essentially act as virtual gateways, allowing users to cloak their true location and access content that may otherwise be off-limits. This not only enhances user freedom and access to information but also ensures a seamless online experience regardless of geographical constraints.
Online privacy concerns are increasing— with giants like Google tracking a significant portion of web traffic — maintaining anonymity online has become a priority for many, including businesses, NGOs, researchers, and journalists. Proxies play a key role in this regard by handling user traffic and obscuring online activities from prying eyes. With the increasing sophistication of online tracking mechanisms and data collection practices, individuals and organizations are seeking ways to safeguard their digital identities and protect sensitive information from unauthorized access.
As cyber threats and privacy breaches continue to make headlines, the demand for secure and private online interactions has never been higher. Proxies offer a layer of protection by serving as a shield against intrusive surveillance and data mining efforts. By redirecting internet traffic through alternate IP addresses, proxies create a barrier between users and potential threats, allowing individuals to browse the web with peace of mind.
Proxies empower users to take control of their online presence and limit the exposure of their digital footprint. Whether it's preventing targeted advertisements, circumventing censorship, or safeguarding confidential communications, proxies can be a great tool for preserving privacy and anonymity in a data-driven world.
While proxy servers offer numerous advantages, it's essential to acknowledge their limitations as well. One significant drawback is that proxy servers typically only handle specific types of traffic, primarily focused on web browsing and specific applications. This means that other forms of online activities, such as email communication or file transfers, may not be routed through the proxy server.
This restriction can pose a challenge for users who require a more comprehensive solution for their internet traffic. For instance, if you rely heavily on sending and receiving emails or transferring files securely, a proxy server may not be the most suitable choice. In such cases, a VPN would be more appropriate, as it encrypts all internet traffic, ensuring a higher level of security and privacy for a wider range of online activities.
There are certain scenarios where using a proxy server may be more suitable than a VPN. Here are some examples:
If you're looking to mask your IP address for specific applications or websites rather than all internet traffic, a proxy server is an ideal choice. This is particularly useful for tasks like web scraping, where you might not need the additional encryption and privacy a VPN provides. Configuring a proxy server on a per-application basis allows for more granular control over your online identity without impacting the speed or encryption of other internet activities.
Proxy servers can be extremely effective for bypassing geo-restrictions to access region-locked content, such as streaming services or news websites. By connecting to a proxy server located in a region where the content is available, you can access it as if you were physically located there. This is a simple and often faster alternative to VPNs, which might not always provide the same level of access due to VPN blocking measures employed by some services.
In environments where multiple users are accessing the same online resources, a proxy server can significantly improve network performance. By caching frequently accessed content, proxy servers reduce the need for repeated downloads from the internet, saving bandwidth and improving loading times. This makes proxy servers particularly useful in corporate or educational settings where network efficiency is necessary.
Circling back to the opening discussion about the staggering projected costs of cybercrime, it's clear that enhancing online security and privacy is not just important—it's necessary. Proxy servers, as we've unpacked throughout this blog, is a solid option for providing the perfect blend of anonymity, efficiency, and access that is vital in modern times.
Businesses don’t have to face the attendant cybersecurity risks alone — cybersecurity experts like Turn-key Technologies, Inc. (TTI) can support enterprise IT teams as they meet emerging cybersecurity challenges. Our certified team of experts can help you secure your network against the unique threats. TTI holds 30 years of experience in network management and security. No matter the size or structure of your organization, we’re here to help you adapt — quickly and successfully — to evolving enterprise workforces.
%20(1).png)
The oil and gas industry is one of the most crucial sectors for global economic stability, but it's also one of the most vulnerable to security...
%20(1).png)
The oil and gas industry is a cornerstone of global energy supply and economic stability, making infrastructure security paramount. From pipelines to...
%20(1).png)
The physical security market is experiencing significant growth, with projections indicating it will expand at a CAGR of 8.03% from 2023 to 2028,...